randomlock
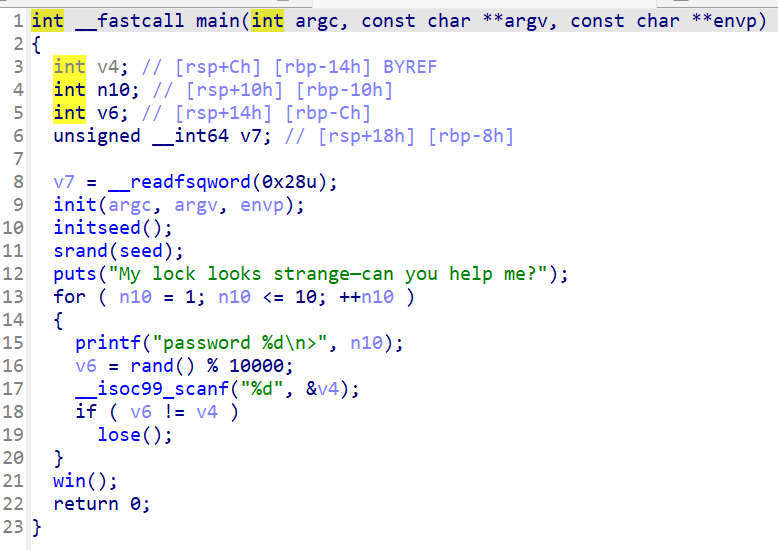
main函数:
initseed函数:
.png)
change函数:
.png)
这题检查随机数通过就给我flag,我们看到initseed函数刚开头是一个真随机的过程,但是我们可以看到,对真随机出的seed进行了seed = seed % 0x64 + 1;模运算并+1,那seed其实就被限制在了[1,100],那我们可以直接设定这个取出来的seed就是1,后面就是照着脚本的操作对seed进行操作,然后循环连接,当有一次随机出的种子是1时就能getflag,这里后面的操作其实是考拉兹猜想,无论是[1,100]中的哪个数最后都会变成1,但是我们没看出来也可以不用管,因为[1,100]范围太小了,就尝试循环爆破也行
模拟的c脚本:
#include <stdio.h>
#include <stdlib.h>
unsigned seed = 2;
void change()
{
if ((seed & 1) != 0)
{
seed = 3 * seed + 1;
}
else
{
seed >>= 1;
}
}
void get_seed()
{
int result;
for (int n120 = 1; n120 <= 120; ++n120)
change();
while (1)
{
result = seed & 1;
if ((seed & 1) != 0)
break;
change();
}
srand(seed);
}
int get_v6()
{
return rand() % 10000;
}
EXP:
from pwn import *
import sys
context(arch='amd64', os='linux')
file_name = './pwn'
elf = ELF(file_name)
gdb_ = 1 if ('gdb' in sys.argv) else 0
switch = 1 if ('remote' in sys.argv) else 0
debug = 0 if ('deoff' in sys.argv) else 1
if switch:
target = '127.0.0.1'
port = 41631
p = remote(target, port)
else:
p = process(file_name)
if debug:
context(log_level='debug')
if gdb_ and switch == 0:
gdb.attach(p)
pause()
s = lambda data : p.send(data)
sa = lambda delim, data : p.sendafter(delim, data)
sl = lambda data : p.sendline(data)
sla = lambda delim, data : p.sendlineafter(delim, data)
r = lambda numb=4096 : p.recv(numb)
ru = lambda delim, drop=True : p.recvuntil(delim, drop)
rl = lambda : p.recvline()
lg = lambda name, data : log.success(name + ': ' + (hex(data) if isinstance(data, int) else data.decode(errors='ignore') if isinstance(data, bytes) else str(data)))
ra = lambda t=None : p.recvall(timeout=t)
cl = lambda : p.close()
it = lambda : p.interactive()
uu64 = lambda data : u64(data.ljust(8, b'\x00'))
#################################################################################
from ctypes import *
while True:
try:
if switch:
target = '127.0.0.1'
port = 41631
p = remote(target, port)
else:
p = process(file_name)
lib = cdll.LoadLibrary('./tes3.so')
lib.get_seed()
for i in range(10):
v6 = lib.get_v6()
sla(b'>',str(v6).encode())
result = ra(1)
if b'{' in result or b'flag' in result or b'win' in result:
lg("flag",result)
it()
break
else:
cl()
except EOFError:
cl()
continue
except Exception as e:
cl()
continue
题目链接:
CTF-Writeups/MoeCTF2025/ randomlock at main · Zenquiem/CTF-Writeups
randomlock
https://zenquietus.top/archives/wei-ming-ming-wen-zhang-YcpaDHHw